This article will be helpful for those developers who are trying to integrate multiple accounting tools with a custom web or desktop application; with the accounting tool database exposed either using ODBC/JDBC or APIs.
The solution was explored when I worked in a project where there was a need to automate the data transmission (bi-directional) between different accounting tools (like Adagio, QB Desktop and Online version, etc.) interfacing with a central database. And make it possible for devices (like iPhone) to transmit data to the central database and subsequently to the accounting tools. In a nutshell, the main application, devices and multiple accounting tools needed to be in sync all the time/whenever required.
……………………………………………………………………………………………………
The Solution
The major features that were provided/implemented:
- Connector: it acts as a bridge between web API and desktop/online accounting tool.
- Data transmission between different entities using customized XML
- Logging request and response on each event with a different status
- The parser in the background (it basically parses the data from XML and maps it with the database)
- Common database structure to handle request and response for different tools
Following diagram shows the flow and integrations process-:
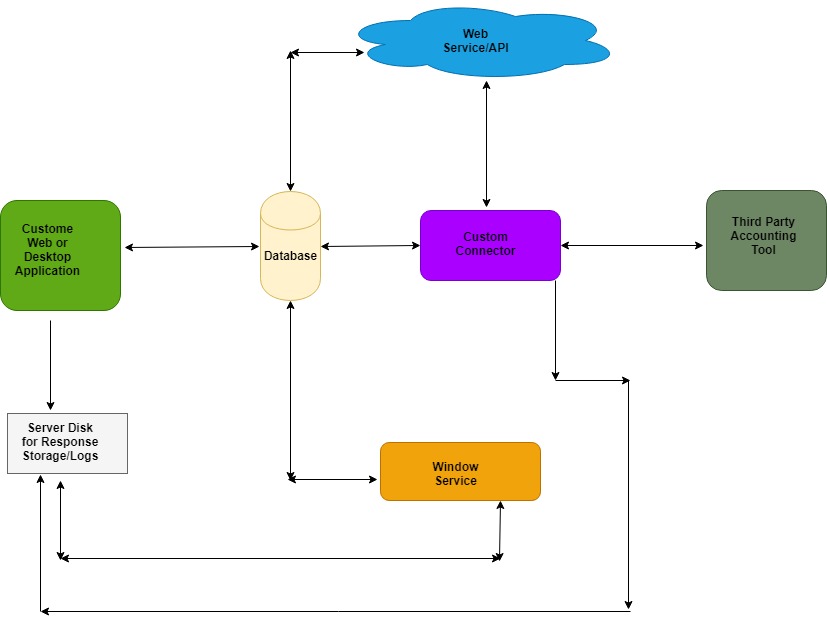
Here, the user has the freedom to use different custom applications based on need. For e.g. in some cases where the API is exposed to the outside world for web accounting tools, we can merge the request-and-response processes in one place along with the parsing of data.
#1 Window Service
It is being used for parsing data coming internally from accounting tool in a specified format. Here, the approach can change as per need because sometimes the customer doesn’t want to put extra load on the server; then we can do it at the same level (i.e. in the request-and-response process).
#2 Web Service/Web API
It is used for running the connector. Actually, the connector will act as a bridge between the accounting tools and the central database.
#3 Main web or window application-
Here we need to have one page which will facilitate the user to generate requests in specified formats (XML or JSON) for required entities (like retrieving customer data or adding a new customer in the Accounting tool).
#4 Accounting tool
Accounting tool which exposes database/API to the outside world. Nowadays most of the applications have shared API or database to the outside world for integration with other applications.
The diagram below describes the data flow between different applications in a stepwise manner:
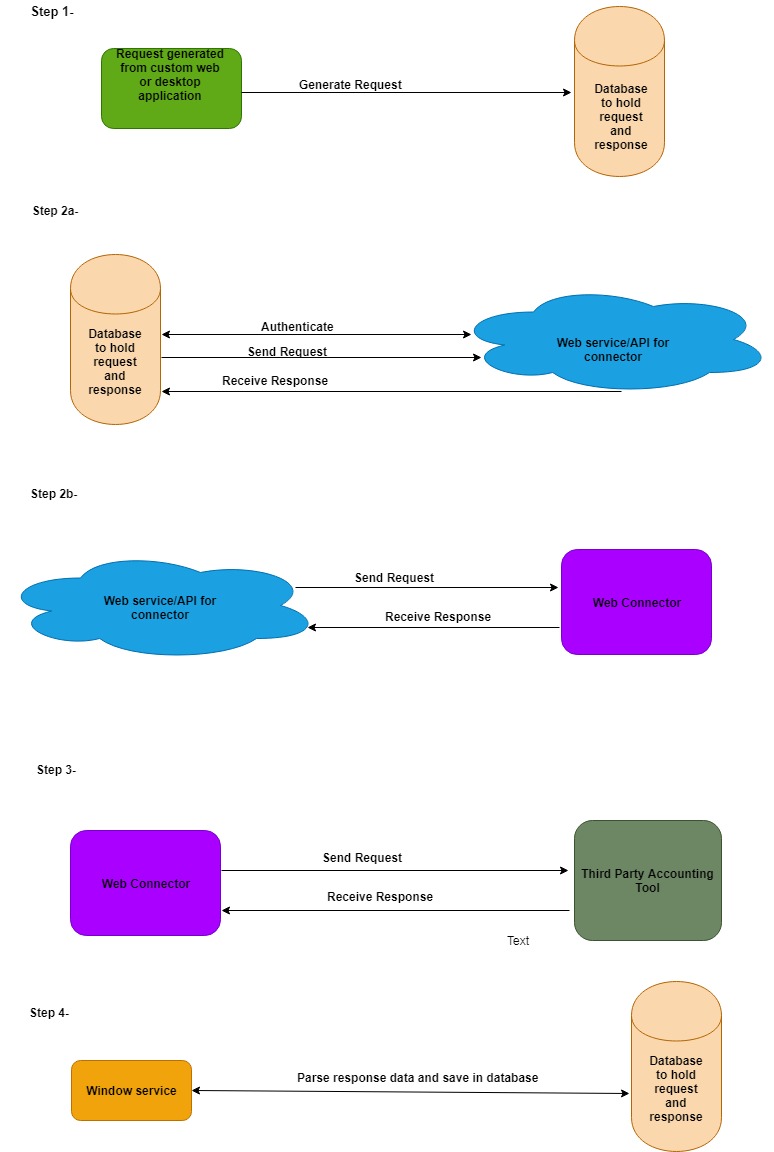
……………………………………………………………………………………………………
Error handling and Logs
Since accounting tools are being used here, it means there are bound to be information pertaining to the flow of money involving different vendors and stakeholders. This section thus holds a lot of relevance. The provision for logging is done either in the database or somewhere else on the disk. Since there different levels and sublevels like web service/API for connector has 4 important sublevels (Authenticate(), SendRequest(), ReceivedResponse() and CloseConnection() ), it is highly relevant to know at every step exactly what data got processed. Also, the availability of results opens up the provision for performing analyses later, whenever needed. Logging makes it possible to handle internal errors as well.
Security Handling
The whole solution should follow the security rules as per the industry norms like SSL implementations for all web-based calls, Cryptographic methodology (wherever required), AntiForgery checks once session established, etc.
……………………………………………………………………………………………………
The views and opinions expressed in this article are those of the author. To know more about our company, please click on Mindfire Solutions.